Plug & Charge Deep Dive: Simplifying the EV Charging Experience
2025年12月17日
VDV 261 Explained: Defining the New Standard for Electric Bus Preconditioning and Smart Charging
2025年12月17日ISO 15118 Plug & Charge Deep Dive:
Building a Safer, More Convenient Charging Ecosystem
"Plug & Charge" is a technical concept originally introduced by the ISO 15118 international standard, aiming to provide a future-proof solution for charging electric vehicles (EVs). This concept enables a more user-friendly and secure way of charging, applicable to all charging stations that fully support the standard.
It is worth noting that it applies not only to wired charging (AC and DC) but also to wireless charging scenarios. With this foundation, let's dive into the details. This article aims to give you a thorough understanding of the entire ecosystem behind Plug & Charge and how it will impact your business model.
The Cryptographic Foundation of Plug & Charge
The power grid is critical infrastructure, and every device connected to it—including electric vehicles and charging stations—needs protection against potential attacks. Imagine if the vast amount of information and billing data during the charging process could be tampered with by a third party; user trust in the charging infrastructure would collapse instantly.
This is why the Plug & Charge process requires the EV and the charging station to establish and share a secure communication link. To ensure a successful Plug & Charge session, both parties must perform a series of operations to guarantee three things:
- Confidentiality: Encrypting and decrypting messages to ensure no third parties or malicious actors can eavesdrop on the communication.
- Data Integrity: Detecting whether received messages have been tampered with during transmission from sender to receiver.
- Authenticity: Verifying that the identity of the communication counterpart (EV or charging station) is consistent with who they claim to be.
Hybrid Encryption Systems: The Three Pillars of Security
ISO 15118 specifies a set of symmetric and asymmetric encryption algorithms to ensure the necessary level of confidentiality and to verify the integrity and authenticity of exchanged data.
1. Confidentiality via Symmetric Encryption
Confidentiality is achieved through symmetric key algorithms, where the sender uses a single (symmetric) key to encrypt the message, and the receiver uses the exact same key to decrypt the ciphertext. This requires that the EV and the charging station must negotiate and agree on using the same symmetric key at the beginning of every charging session.
2. Authenticity & Integrity via Asymmetric Encryption
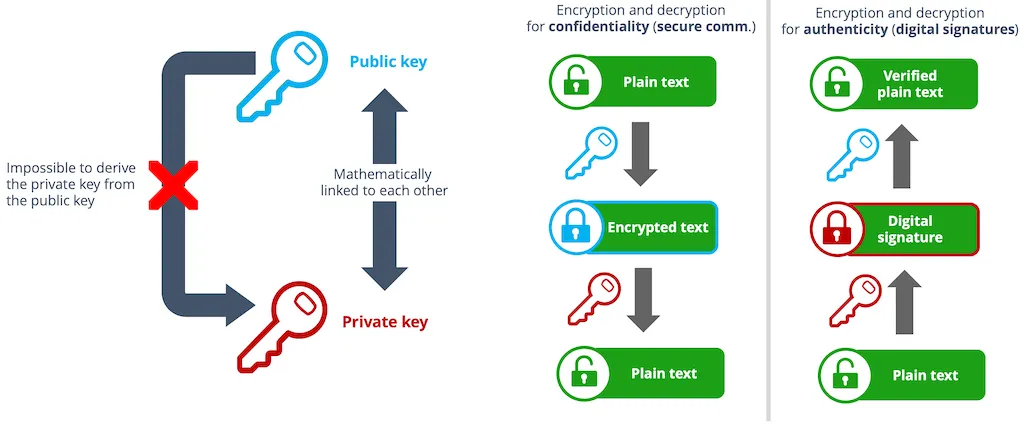
On the other hand, verifying authenticity and data integrity can only be achieved through asymmetric encryption. Asymmetric encryption uses a pair of keys: a Private Key and a Public Key.
- These two keys are mathematically related: messages encrypted with the public key can only be decrypted with the corresponding private key, and vice versa.
- The Private Key must be kept strictly confidential and used only by the owner to create digital signatures.
- The Public Key is distributed to other peers in the ecosystem to verify signatures created by the associated private key.
This process ensures that the EV and the charging station can establish trust in the authenticity and integrity of the messages sent to each other.
Specific Algorithm Implementation in ISO 15118
ISO 15118 follows a generic hybrid approach: using asymmetric algorithms to create/verify digital signatures and negotiate symmetric keys, and then using that symmetric key to encrypt/decrypt all messages during the charging session. Specific technical parameters are as follows:
- TLS v1.2: The Transport Layer Security protocol used to establish the encrypted communication session.
- ECDH (Elliptic Curve Diffie-Hellman): A key exchange protocol used by both parties to negotiate a shared (symmetric) TLS session key.
- AES-128: Using symmetric block ciphers AES-128-CBC (ISO 15118-2) or AES-128-GCM (ISO 15118-20), utilizing the aforementioned TLS session key to encrypt and decrypt all messages.
- ECDSA (Elliptic Curve Digital Signature Algorithm): Used in conjunction with the SHA-256 hash function to verify the sender's authenticity and message integrity.
⚡️ Technical Pain Points & Solutions
Implementing ECDH key exchange, AES encryption, and ECDSA signature verification on embedded devices is not only difficult to develop but also places strict demands on hardware performance.
The Charge Bridge Hardware Module features a built-in hardware cryptographic acceleration engine that perfectly supports all encryption algorithms specified by ISO 15118. You don't need to delve into the complex cryptographic underpinnings to equip your charging pile with financial-grade secure communication capabilities.
Public Key Infrastructure (PKI): The Foundation of Plug & Charge
ISO 15118 outlines a digital certificate ecosystem, which is a prerequisite for Plug & Charge operation. This is where the Public Key Infrastructure (PKI) comes into play.
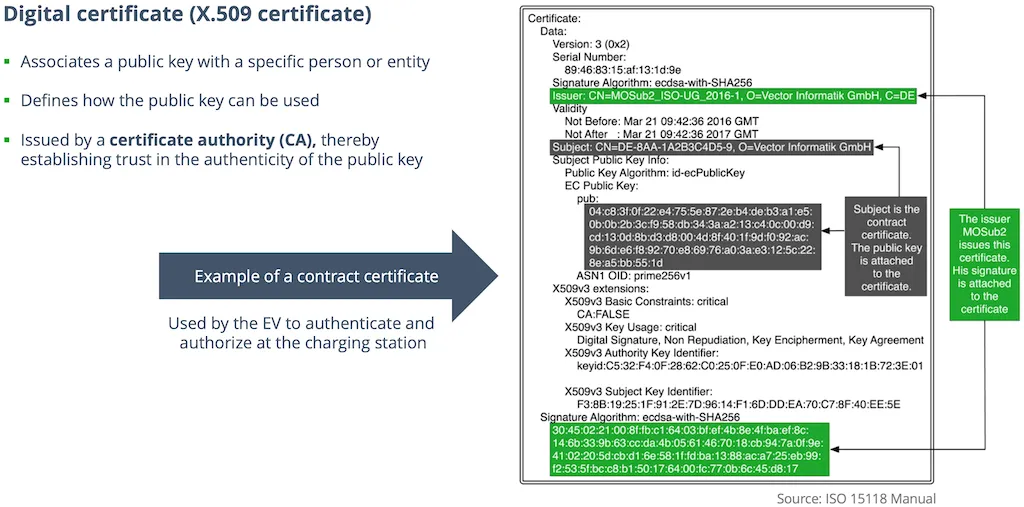
PKI is a tree-like, hierarchical structure composed of trusted third parties known as Certificate Authorities (CAs). These CAs are responsible for managing the creation, storage, distribution, and revocation of digital certificates. A digital certificate is an electronic document used to verify that a public key belongs to an authorized party.
We can use a building's security system as an analogy: You present your ID card to a card reader at the entrance. The certificate stored in the card allows the reader to verify if you are permitted to enter the building. The purpose of establishing a PKI is to provide a framework: verifying the identities of people and devices, enabling confidential communication, and guaranteeing controlled resource access.

In the case of ISO 15118, certificates used for verification and access authorization are issued to EVs, charging stations, and other market participants critical to the Plug & Charge process. As a trusted third party, any CA has the responsibility to verify the identity of the certificate holder before issuing the corresponding certificate.
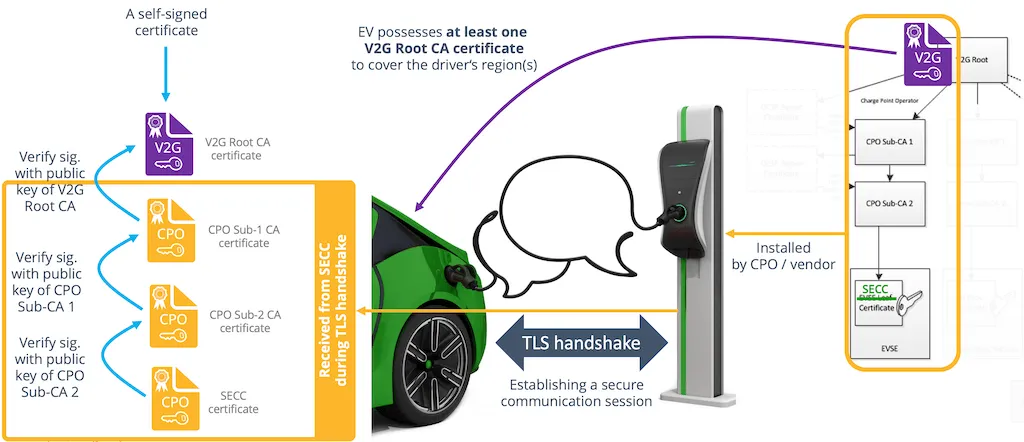
Establishing Trust via TLS Handshake: The CPO Example
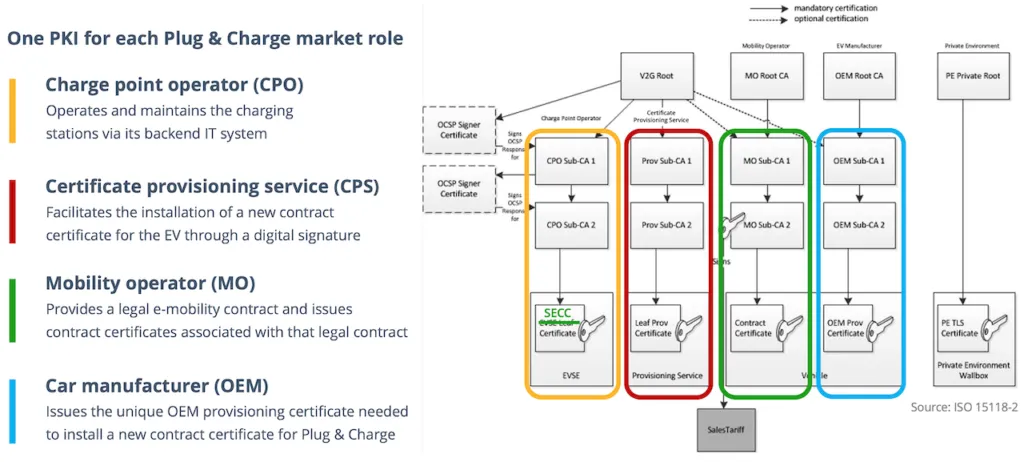
Let's use a Charging Point Operator (CPO) as an example to illustrate the process of establishing a trust chain:
- V2G Root CA (Trust Anchor): Acts as the top-level trust anchor. All market participants in this PKI set need to consider the V2G Root CA as a trustworthy organization.
- Sub-CA: The V2G Root CA issues and signs certificates for Sub-CAs (e.g., CPO Sub-CA 1, an international charging operator). Subsequently, this Sub-CA might issue certificates for the next level Sub-CA (e.g., CPO Sub-CA 2, the national division of that operator).
- SECC Certificate (End-entity): CPO Sub-CA 2 finally issues and signs the SECC certificate (also referred to as the Charging Station Certificate in ISO 15118). The SECC is the control unit running the ISO 15118 communication protocol.
ISO 15118 mandates that every PKI requires at least one and at most two Sub-CAs to establish the trust chain between the Trust Anchor (Root) and the End Entity (Leaf). It is common security practice that Root CAs never directly issue end-entity certificates.
The TLS Handshake Process
At the start of a Plug & Charge communication session, the EVCC (vehicle side) and SECC (charger side) need to establish an encrypted session, known as the TLS Handshake. During this process, the charging station presents its certificate set (SECC certificate, CPO Sub-CA 1 certificate, and optionally CPO Sub-CA 2 certificate) to the vehicle to prove it is a trustworthy charging station.
The vehicle then needs to verify the digital signatures of all certificates—tracing back from the SECC certificate all the way to the pre-installed V2G Root CA certificate—and check if any certificates have expired. If all verifications pass, the TLS session is successfully established.
Contract Certificates: The Key to Seamless Authentication & Authorization
Before the charging station allows the EV to charge, the vehicle needs to present a valid Contract Certificate to gain authorization.
This contract certificate is linked to a billing account via a unique identifier, known as the Electric Mobility Account Identifier (EMAID). For example, an EMAID might look like 'DE-8AA-1A2B3CD5-9'.
The car owner needs to sign a contract with a Mobility Operator (MO) (also known as EMSP or EMP) to create a billing account. The MO is then responsible for provisioning the contract certificate into the EV through a series of carefully orchestrated steps.
VDE Application Guide VDE-AR-E 2802-100-1: The Ecosystem Blueprint
ISO 15118 only defines the direct message exchange between the EV and the charging station (e.g., "Certificate Installation Request/Response" message pairs). However, to issue and correctly install the aforementioned contract certificate into the EV, more market roles are involved, including Mobility Operators (MO), Charging Point Operators (CPO), and Original Equipment Manufacturers (OEM).
The interactions between these roles are not fully defined in the ISO 15118 specification. This is exactly where the VDE Application Guide VDE-AR-E 2802-100-1 comes into play: this guide fills the gaps in the specification and serves as the blueprint for establishing a complete and coordinated Plug & Charge ecosystem.
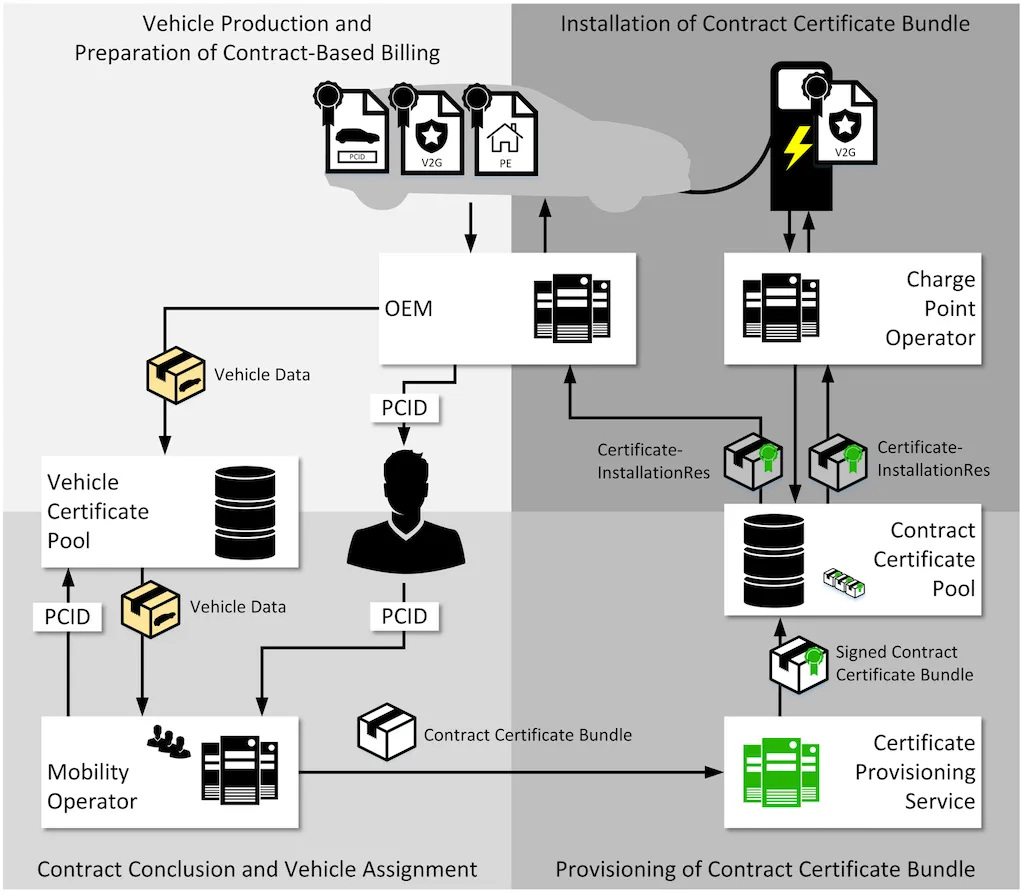
For your product or service to actively participate in the Plug & Charge ecosystem, you need to establish corresponding business processes and implement interfaces with other market roles in this interconnected system architecture.
One of the market-ready Plug & Charge and PKI ecosystem operators currently is Hubject. Additionally, more companies (such as e-clearing.net) are committed to providing the necessary services to foster the development of this PKI ecosystem.
In the diagram above, besides the well-known market roles (OEM, CPO, MO), you will notice some new roles, such as Data Pool Operators and Certificate Provisioning Service. All these independent roles work closely together to ensure the entire ecosystem runs like a well-oiled machine.
⚡️ Charge Bridge: Instantly Unlock Plug & Charge Capabilities
Facing complex VDE backend processes and multi-party interface integration, the Charge Bridge Hardware Module is fully Plug & Charge ready.
We have not only implemented the complete ISO 15118 communication protocol at the low level but also pre-configured docking interfaces with mainstream ecosystems like Hubject. Without starting development from scratch, we help your charging equipment instantly acquire full "Plug & Charge" functionality and rapidly integrate into the global PnC network.